Level Up Your Microservices Security: Service Mesh + AMTD
Service mesh has become a game-changer for managing communication in complex microservice architectures. They bring order, security features like encryption, and simplified traffic management. But are service meshes a security panacea? Unfortunately, no. While they offer strong built-in protection, a determined attacker can still find ways to exploit vulnerabilities, especially if the mesh is misconfigured.
This is where Automated Moving Target Defense (AMTD) steps in as your secret weapon. Imagine a constantly shifting castle, making it nearly impossible for attackers to lay siege. That's the essence of AMTD. It dynamically changes the attack surface of your services, leaving attackers confused and empty-handed.
The Achilles' Heel of Service Meshes
Service meshes excel at securing communication between services. However, they have a few vulnerabilities:
Misconfigurations: A single mistake in the mesh configuration can create an opening for attackers.
Static Nature: Attackers can potentially study a static configuration and plan their exploit.
Control Plane: The control plane, which manages the mesh, can itself be a target for attacks.
Enter AMTD: The Dynamic Defender
AMTD works by continuously changing elements of your service environment, like:
IP Addresses: Services and the control plane can dynamically switch IP addresses, making it difficult for attackers to target them.
Ports: Communication ports used by services can be constantly shuffled, further confusing attackers.
Service Locations: In some AMTD implementations, even the physical location of services within the network can be shifted.
This constant movement disrupts attackers who rely on a static understanding of your system. Imagine trying to hit a moving target – that's the challenge AMTD presents.
A Deeper Look: Service Mesh vs Service Mesh with AMTD
Let's take a closer look at the security posture with a service mesh alone compared to one that incorporates AMTD:
Service Mesh Only:
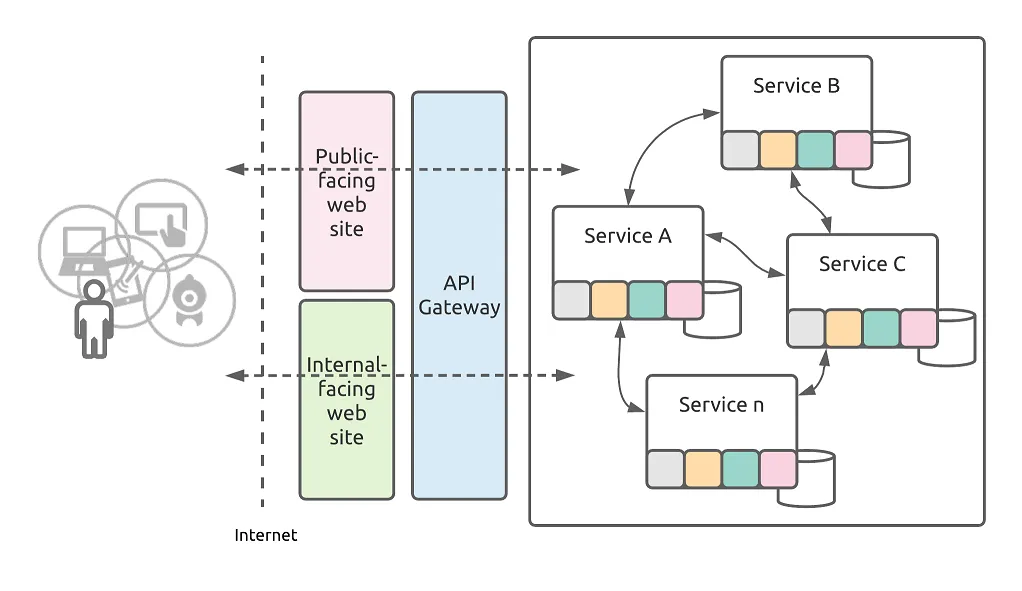
A Microservices-based Solution without the Service Mesh architecture
A service mesh acts as a central hub for communication between microservices.
It enforces security policies like encryption and authorization.
However, the configuration and the communication paths are static, making them vulnerable if exploited.
Service Mesh with AMTD
Here, instead of a static communication path, let's visualize the dynamic nature introduced by AMTD:
AMTD adds an extra layer of dynamic defense.
It constantly changes elements like IP addresses, ports, and potentially even service locations.
This creates a moving target, with the dotted arrow representing the dynamic communication path that attackers can't lock onto.
The Fire-and-Forget Security Layer
The beauty of AMTD is its "fire-and-forget" nature. Once configured, it runs autonomously, constantly adapting your defenses without needing constant human intervention. This frees up your security team to focus on other critical tasks.
The Perfect Security Match: Service Mesh and AMTD
Think of service meshes as your frontline defense, providing core security features like encryption and authorization. AMTD acts as your second line of defense, constantly shifting the landscape and making attackers' efforts futile. Together, they create a powerful security posture for your microservices.
Ready to Take Your Security to the Next Level?
Service meshes are a great foundation for securing microservices, but don't stop there. Consider AMTD as your secret weapon, the dynamic layer that keeps attackers on their toes. With this combined approach, you can achieve a more robust and resilient security posture for your applications.
Let's discuss!
Have questions or want to learn more about AMTD and service meshes? Leave a comment below and let's get the conversation started.
#cloudsecurity #microservicessecurity #cybersecurity #devsecops #appsec
#service mesh #istio #soloio #amtd #automatedmovingtargetdefense
#fireandforgetsecurity


No comments.